Degree Projects
We are seeking potential candidates who can join our research team to work on intriguing and significant research projects. We can also assist you in addressing your identified research problem(s). If you are interested in working with us, kindly contact Prof. Andrei Gurtov.
Title: SDN-based Dynamic QoS Routing in UAV Communication Networks.
Description: Ensuring secure and reliable communication in UAV networks is challenging due to frequent topology changes, variable link quality, and limited bandwidth. This thesis proposes a Software-Defined Networking (SDN) approach for dynamic Quality of Service (QoS) routing in UAV communication systems. Using SDN controllers (e.g., Ryu, ONOS), the system will dynamically adjust routing paths based on real-time network metrics and application priorities. The student will implement a simulation or emulation testbed using OMNeT++ or Mininet or CORE to evaluate performance under different network conditions, including link degradation and temporary node outages.
Keywords: SDN, UAV networks, QoS routing, adaptive networking, reliability.
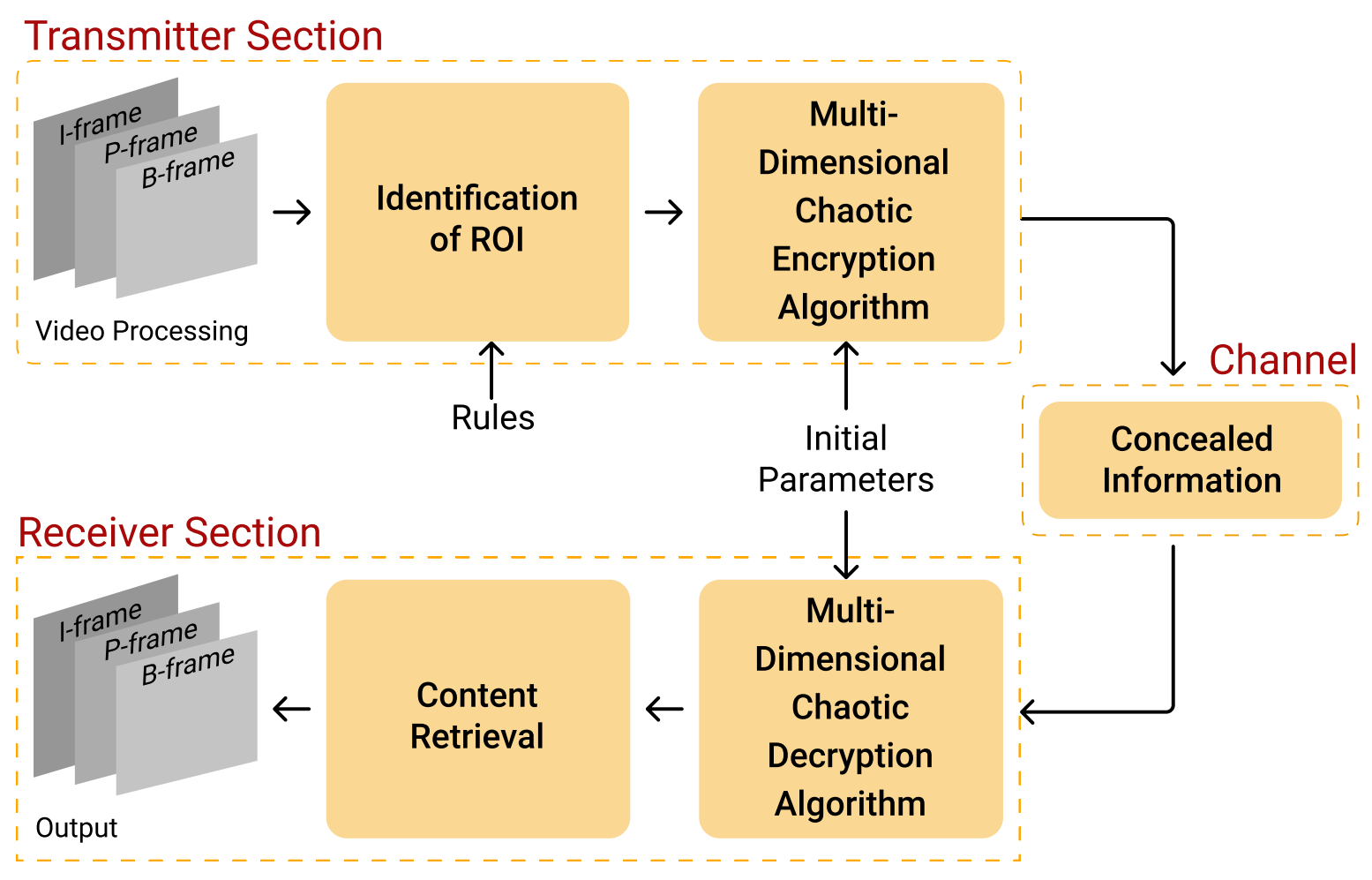
Title: Selective Chaos Encryption: Efficient Video Security for Smart Cities.
Description: Smart cities generate massive volumes of multimedia data daily through surveillance cameras, sensors, and monitoring systems. Protecting this sensitive video information is critical; however, traditional encryption methods, which process entire video streams, are often computationally intensive and time-consuming. To address this challenge, this project proposes a novel chaos-inspired encryption framework specifically designed for secure and efficient video data transmission in smart city environments. The framework processes video streams frame by frame, intelligently identifying Regions of Interest (RoI) using customizable detection rules. Only these sensitive regions are selectively encrypted using diverse chaotic maps, enhancing robustness while significantly reducing computational overhead and processing time. After encryption, frames are recombined into a complete video stream, which is transmitted in standard video formats. On the receiving end, the encrypted frames are separated, decrypted by reversing the chaotic transformations, and accurately reassembled to reconstruct the original video. This project provides hands-on experience in multimedia processing, chaos theory, computer vision-based RoI detection, and targeted encryption techniques, preparing students to develop innovative solutions for the rapidly evolving field of smart city security.
Title: Simulation Framework for Resource Allocation Strategies in UAV Communication Systems.
Description: Modern UAV applications—such as environmental monitoring, infrastructure inspection, and emergency response—depend on efficient and adaptive communication strategies. This thesis aims to develop a flexible simulation framework for evaluating resource allocation techniques (e.g., bandwidth, channel prioritization, latency thresholds) in UAV communication systems. The framework will support customizable scenarios and allow exploration of both rule-based and optimization-based strategies. Tools such as OMNeT++, SimPy, or custom Python-based simulations will be used to analyze communication performance under varying operational conditions.
Keywords: UAV communication, resource allocation, adaptive networks, simulation, bandwidth optimization.

Title: SDN-based Resilience Framework for UAV Communication Networks in Challenging Environments.
Description: Unmanned Aerial Vehicles (UAVs) are increasingly used in scenarios such as disaster response, infrastructure monitoring, and precision agriculture. These applications require robust communication networks that can adapt to rapidly changing conditions, such as signal interference and node mobility. This thesis proposes the design and evaluation of an SDN-based resilience framework for UAV networks. The framework will use centralized SDN control to enable adaptive routing based on real-time link quality and network status. The system will be tested in simulated environments using Mininet or CORE with SDN controllers like Ryu or ONOS, assessing resilience and availability under variable conditions.
Keywords: UAV communication, SDN, network resilience, adaptive routing.
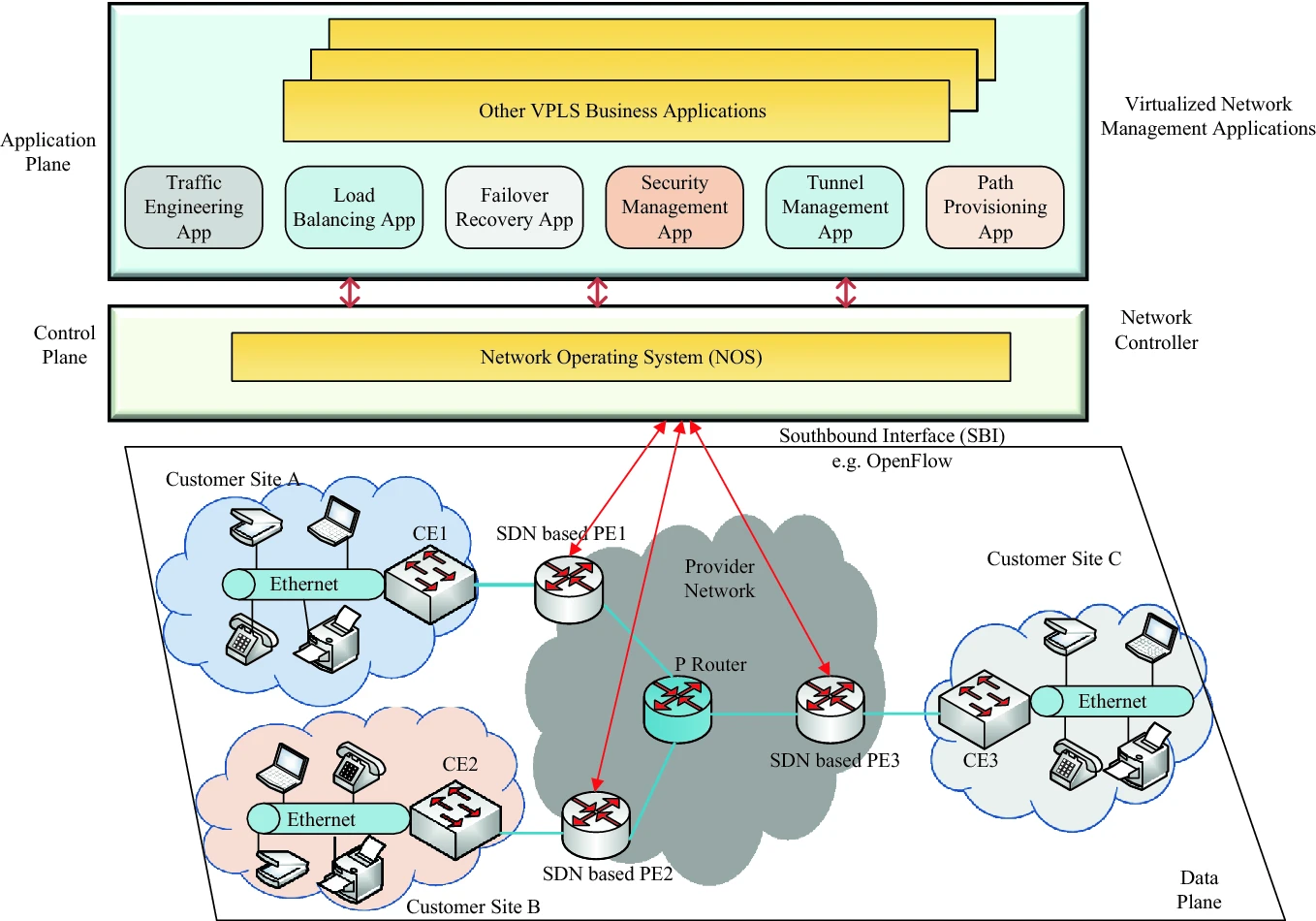
Title: SDN-enabled Tunnel Management of Secure VPLS Network.
Description: Daily, the Internet connects a vast number of devices with diverse needs. Among them are intelligent sensors, control valves, and traffic lights. These devices are often difficult to patch and have known vulnerabilities. Consequently, it is essential to conceal these devices from the public Internet while permitting authorized access for remote data administration and updates. Secure Virtual Private LAN Services (VPLS) are gaining popularity as a means of securely connecting geographically dispersed devices to a shared LAN network that is isolated from the Internet. Traditional IP routing protocols cannot provide such a connection; thus, an overlay network of encrypted HIP/IPsec tunnels may be utilized instead (as shown between PEs routers in the figure). However, the tunnel construction procedures of traditional VPLS designs are inflexible, static, and costly. Consequently, secure VPLS designs have drawbacks including excessive network resource use, high tunnel formation time, and high operating cost. In this thesis, by leveraging the benefits of Software-Defined Networking (SDN), we focus on proposing a novel secure SDN-enabled VPLS architecture with an improved tunnel management mechanism to control the tunnel time out based on tunnel creation and maintenance cost. The main simulation tools expected to be used in the thesis include mininet (or CORE simulator) and SDN controller (e.g., Ryu, Onos).
Title: A Scalable Secure VPLS Architecture for Industrial Internet.
Description: VPLS is a Layer 2 Virtual Private Network (L2VPN) used in industrial and corporate networks for applications such as Data Centre Interconnect (DCI), video conferencing, Voice over Internet Protocol (VoIP), and Internet Protocol Television (IPTV). HIPLS is the secure VPLS architecture that includes a logical security layer for VPLS security service management. The provider constructs a full mesh of Host Identity Protocol (HIP) tunnels in HIPLS to link PEs, as depicted in figure - A below, depicting a HIPLS network with four sites. However, this reachability paradigm leads to the expansion of routing tables in PEs. The notion of relaying may be used to reduce the expansion of routing table entries. The relaying technique picks a limited fraction of PEs as hub nodes while preserving mesh-wide connectivity. This enables spoke PEs (non-hub) to communicate with other PEs by relaying via a chosen hub PE (Figure - B) and consequently reducing the entries for the routing table in spokes. This thesis focuses on the placement problem (what is the optimal location of Hubs to reduce the network cost of relaying in the HIPLS network when failure happens in spoke-to-hub communications. Moreover, SDN will be employed for the establishment of a spoke-to-hub connection and backup path selection between spokes to hubs when facing a failure. The thesis is expected to include the implementation of proof-of-concept. The main simulation tools expected to be used in the thesis include mininet (or CORE simulator) and SDN controller (e.g., Ryu, Onos).

Title: Performance Evaluation Through Experimentations for HIP.
Description: Host Identity Protocol (HIP) is a networking architecture that aims to implement the identifier/locator split. The HIP architecture has been designed to re-establish traditional networking, enabling hosts to communicate in today's highly complex communication environment with IPv4, IPv6, and other middleboxes. HIP offers built-in support for mobility, multi-homing, and security. It improves the IP architecture by establishing a Host Identity (HI) namespace between the IP and transport protocols. Since HIP comprises end-to-end security, mobility, and multi-homing, our primary focus in this thesis is the performance evaluation of the integration of VPLS with the HIP known as HIPLS. Moreover, by considering the multiple use cases of HIPLS in the industry (e.g., critical manufacturing, transportation system, public healthcare), such as the ones deployed by Tempered company, we focus on constructing experimentation on our servers for performance evaluation (in terms of networking measurement) of time-sensitive applications under HIPLS deployment as well as HIP mobility test cases, HIP base exchange test cases, etc. For further info on the deployed HIPLS in multiple industrial sections, please see: Tempered.
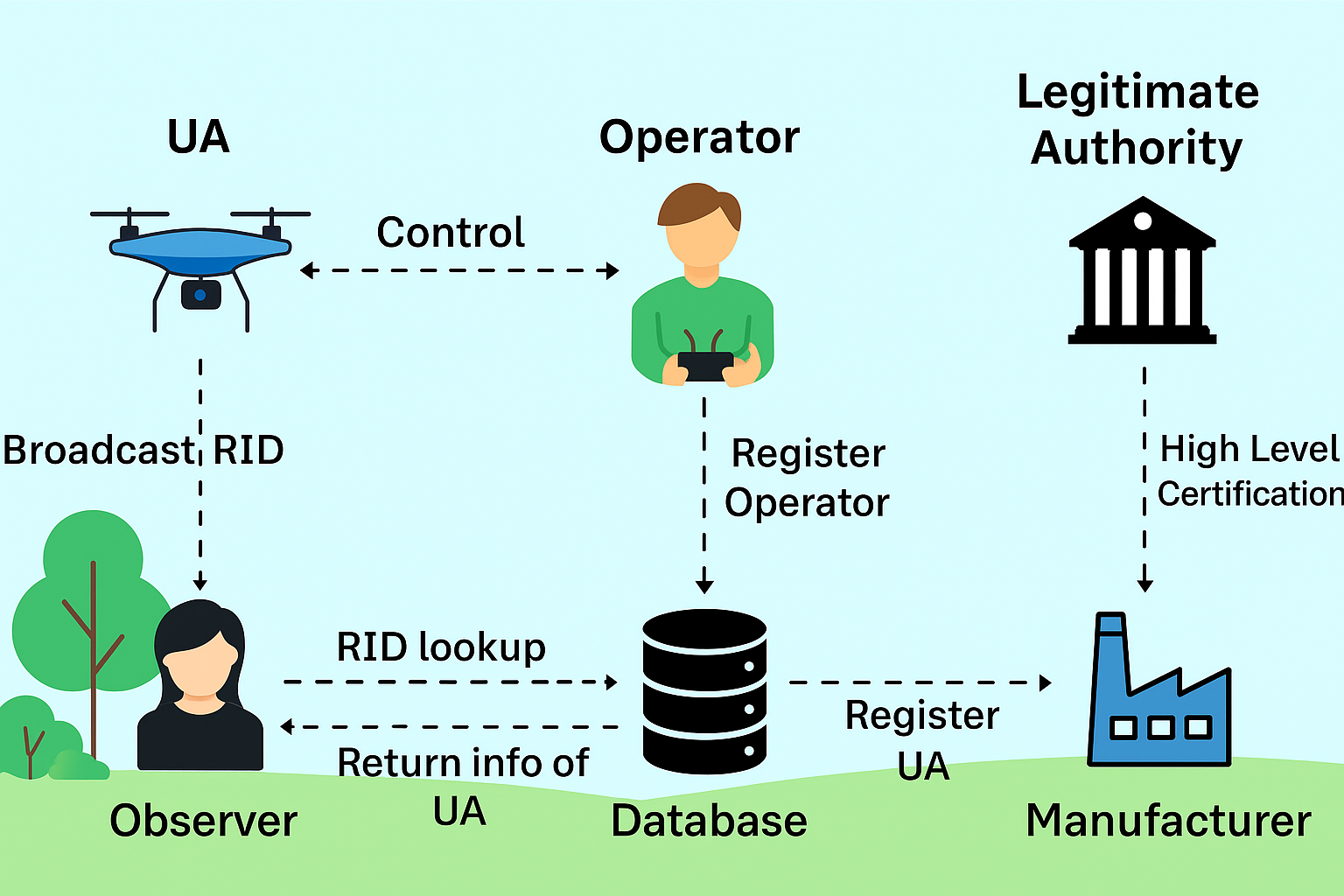
Title: A Lightweight Authentication Framework for Drone Remote Identification Protocol.
Description: The Federal Avionics Administration (FAA) in the United States published a new dedicated regulation called RemoteID, which mandates that operators of Unmanned Aerial Vehicles (UAVs) broadcast messages reporting their identity and location to improve the transparency and traceability of UAV operations. Since these messages are broadcasted in plain text, an attacker can eavesdrop on these messages and impersonate a legitimate drone. The data of the operator is also not anonymous. These attacks can cause serious damage to drone and people on the ground. Therefore, it is important to address security concerns inside RemoteID. This thesis aims to propose a lightweight authentication scheme that focuses on operator anonymity and has minimum effect on the battery budget-comparing the proposed solution with existing literature regarding communication cost and battery consumption.
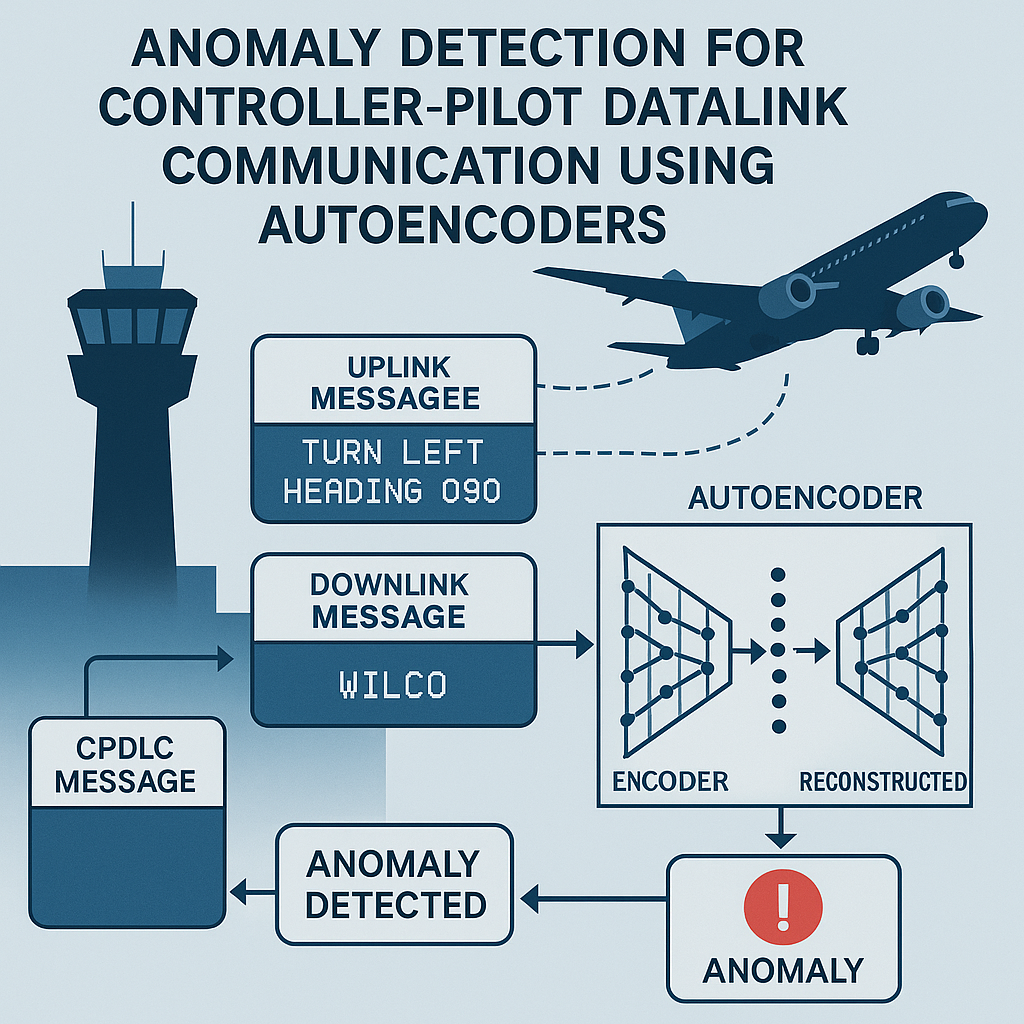
Title: Anomaly detection for Controller Pilot Datalink Communication Using Autoencoders.
Description: Controller-Pilot Data Link Communications (CPDLC) are quickly replacing voice-based Air Traffic Control (ATC) communications across the globe. Because it is digital, CPDLC is robust and bandwidth efficient, making it the perfect solution for busy airports. Although CPDLC seems to be a suitable fit for modern-day ATC operations, it has severe security vulnerabilities. For example, eavesdropping, spoofing, man-in-the-middle, message replay, impersonation attacks, etc. Cyber-attacks on the aviation communication network could be dangerous and cause harm to people, service providers, and the aviation industry. This thesis aims to highlight the shortcomings of CPDLC and work on deep learning-based Auto-Encoders to detect anomalies in CPDLC. We already collected a CPDLC dataset from Arlanda, Airport. The CPDLC collected dataset contains uplink and downlink messages. The final goal is to find an anomaly pattern inside CPDLC messages.
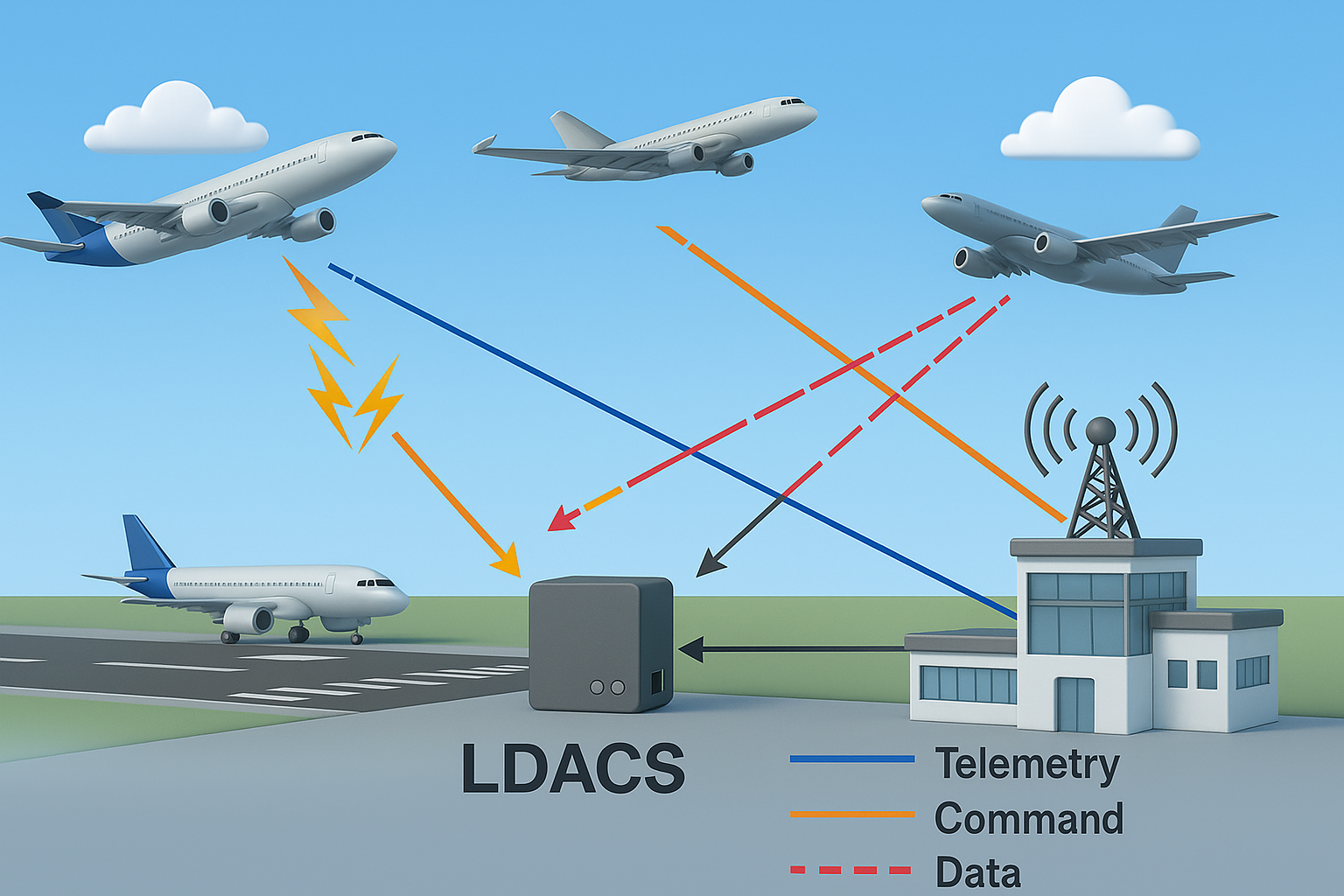
Title: A Realizable Authentication, Key Agreement, and Secure Handover Approach for L-Band Digital Aeronautical Communication System.
Description: The L-band Digital Aeronautical Communications System (LDACS) is the datalink for terrestrial communications related to the safety and regularity of flight. It can be considered the successor to VHF Data-Link mode 2 (VDLm2). LDACS supports two communications modes: (i) an Air-Ground (A/G) link for long-distance terrestrial communication and (ii) an Air-Air (A/A) link for oceanic, polar and remote communications. As demanded by regulatory documents from the International Civil Aviation Organization (ICAO), any datalink providing services via the ATN/IPS must feature sound cybersecurity measures. The cybersecurity architecture of LDACS is based on a dedicated PKI, mutual entity authentication, key establishment, and user and control channel protection. However, secure handover phase between different LDACS network is not discussed in literature. This thesis aims to secure handover between different LDACS subnets hosted by different LDACS network service providers. This thesis also focuses on Round Time Trip (RTT), authentication time and overhead message issues.
Title: Securing Digital Twin for Trustworthy Aeronautics.
Description: Digital Twin (DT) creates a digital footprint to let engineers realize the real-time functional behavior of cyber-physical devices. It brings enormous benefits but with an increased threat horizon. Cyber-attackers can perform reconnaissance scans, spoofing, side-channel, and install malware to harm or take control over physical assets. This project aims to (i) investigate the vulnerabilities within DT in aviation and (ii) propose a lightweight authentication and/or authorization framework using zero-knowledge proofs (ZKP) / blockchain / homomorphic encryption.

Title: Development of a flexible and scalable cyber-attack simulator to train Air Traffic Management (ATM) stakeholders.
Description: The high-end security solutions fail to prevent catastrophes from cyber incidents if the stakeholders have incompetent cyber skills. Finding an appropriate way to educate and train stakeholders is equally important as developing security solutions. In this project, the plan is to develop a customized simulator that allows the administrator to launch various fake cyberattacks on fake realistic aviation environments. The simulator will aid in educating and training ATM actors to recognize and defend against cyberattacks, avoiding accidents and potentially saving lives as well as preventing economic disasters.
Title: Anomaly detection of data streams and decision processes in advanced Digital Air Traffic Service (ATS).
Description: A tiny issue in the interconnected systems, heterogeneous data sources, and advanced AI components of Future Digital ATS could result in false data and incorrect decisions. Thus, it will be important that future Artificial Intelligence (AI) systems understand when data is corrupt and when AI's decisions are unreasonable, i.e., new types of safety nets will be needed to monitor both data sources and AI. Therefore, in this project, the objective is to develop AI solutions that validate the truthfulness of incoming data and assess the reasonableness of the decisions made by an underlying AI.
Page responsible: Andrei Gurtov
Last updated: 2025-06-30

