TDDC90 Software Security
Labs
General information
Sign up for the labs! Sign-up deadline is November 12.
All assignments must be completed (and given a pass by the lab assistant) before the deadline. You will work at your own pace, but we recommend that you participate in the lab sessions and try to complete the labs according to the schedule.
Deadline: December 17:th at 23:59PM. Lab reports handed in after the deadline will be corrected only as time permits
Connecting to the lab VMs
Starting this year, the PONG and WEBSEC labs will run on the new Cybersecurity Lab backend (same as the Ethical Hacking course). Each Webreg group will be assigned one virtual machine on the backend, and each student in a Webreg group will get an account on that VM. Students will connect to their assigned VM using RDP (Remote Desktop Protocol). Login credentials and IP addresses necessary for connecting to the VM will be sent out by email to all students who signed up for labs shortly after the Webreg sign-up deadline.
Note that the VMs can only be reached from one of the LiU Linux lab computers. (Access from home via student VPN will not work.) It is possible to connect via ThinLinc, however.
Setup instructions
- Start the RDP client Remmina
- Create new connection (click the '+' symbol in the top left corner)
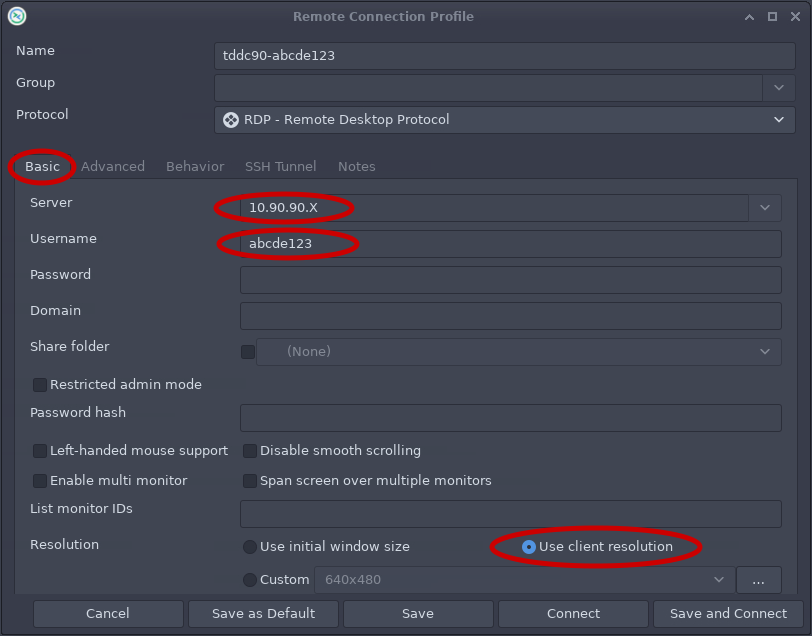
- Under Basic tab (See Fig 1)
- Enter the Server IP that you received in your email.
- Enter username (your liuid)
- Choose Use client resolution
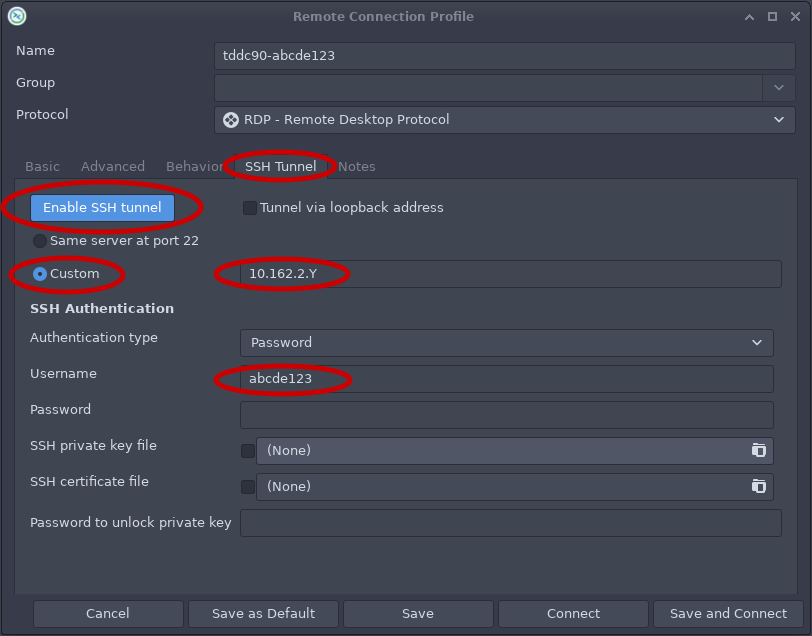
- Under SSH Tunnel (See Fig 2)
- Click Enable SSH tunnel
- Select Custom
- Enter the SSH Server IP that you received in your email.
- Enter username (your liuid)
- Save and Connect, you need to provide your login credentials twice. Use the password you received in the email.
Lab instructions
PONG
This is the largest lab in the course. You will be working with several aspects of software security using the same codebase throughout. The lab is split into three parts that will be submitted separately: Review, Exploit, and Mitigation
Ulf Kargén will supervise this lab.
Lab description: LAB-PONG.pdf
Hand-in instructions: Separate lab reports for each part should be submitted in pdf format to Ulf Kargén (ulf.kargen@liu.se).
Web Security (WEBSEC)
In this lab you will try out some of the vulnerabilities that have been discussed in the course. You will also be given the opportunity to look at how to mitigate the risks that these vulnerabilities pose.
Ulf Kargén will supervise this lab.
Lab description: LAB-WEBSEC.pdf
Hand-in instructions: Lab reports should be submitted in pdf format to Ulf Kargén (ulf.kargen@liu.se).
Static Analysis (STATIC)
Ulf Kargén and Ahmed Rezine (ahmed.rezine@liu.se) will jointly supervise the lab.
Lab description: LAB-STATIC.pdf
Note that this lab will not run on a VM, but on the regular LiU Linux systems. Also note that, even though the lab description instructs to connect to ThinLinc, it works equally well to use the computers in the LiU Linux lab rooms.
Lab files: sana.zip
Hand-in instructions: As part of the lab you will need to demo your solution to Ahmed or Ulf. After being passed on the demo, hand in your lab solution (as a pdf) via email to to the lab assistant that you demoed for.
Code inspection (INSPECTION)
In this assignment you will be conducting a code review of several small pieces of vulnerable C/C++ code in groups of (typically) 6 students. Groups will be formed by randomly combining 3 groups from Webreg during the mandatory (!) seminar on November 27. During the seminar, you will also be required to present some of your findings from the code review, so it is important that you have a solid grasp of the vulnerability types discussed during the memory safety lectures before attending the seminar.
While you are not required to find all vulnerabilities, you are expected to be able to discuss for each piece of code at least
- which vulnerability types are worthwhile looking for, given the APIs and language features used in the code
- what each part of the code does (i.e., how the code works)
- where you suspect that a vulnerability might reside, and why
The Lisam page for the course can be found here. (Click on "Submissions" in the left-hand menu.)
The submission form can be downloaded here
Groups who fail to fulfill the above requirements or students who cannot attend the seminar (due to a valid reason) must complete an extra assignment to pass. If you are unable to attend the seminar, please contact Ulf Kargén well in advance.
Page responsible: Ulf Kargén
Last updated: 2025-11-27

