TDDE61 Ethical hacking
Labs
Overview
The labs are composed of a number of flags (this year, there are 13) that each give a number of points. The sum of points for all flags is 100. If you struggle to capture a flag, you can get hints which will reduce the number of points you get for that flag. To pass the course, you need to complete the first 12 flags and get at least 20 points. Labs are done in pairs.
The lab series in this course corresponds to 4.5 credits which on average corresponds to 120h of work.
Signup
To sign up to the labs you should register for one of the four lab groups (A-D) in Webreg. Deadline to sign up is 2026-01-23.
Assignments
For each flag you need to to three things:
- Find the flag and submit it through CTFd (detailed instructions will come)
- Prepare a short writeup of how you got the flag and submit it in Lisam
- Demonstrate your flag capture to your lab assistant
Flag submission
Flags are submitted using CTFd (link to appear). The flags are unique for each pair of students, so you cannot copy another students flag and submit it. The time when you submit the flag till decide the number of points you get for capturing the flag.
Flag writeup
For each flag you capture, you should also produce a 1-2 page writeup of how you acquired the flag (page length is approximate, some might be a bit longer and some perhaps shorter). The writeup should be submitted no later than one week after submitting the flag. There is a separate submission opportunity for the writeups.
Flag demonstration
To verify that you have done the work yourselves and that both students in a pair have the necessary understanding of the process you also need to demonstrate the flags to the lab assistant. Due to the relative high number of flags, you will not need to go through every flag each time. Instead, you should demonstrate a batch of at least 3 and at most 6 flags at a time. The lab assistant will select some parts of the flags and ask you to explain what you did.
Lab setup
There are two main options to access the lab environemnt. The first is to use the built-in RDP client in the LiU linux lab rooms (including the new cybersecurity lab room). The other is to set up a tunnel connection from a local VM on your own computer. The latter requires you to be physically present at one of LiU's campuses. Finally, there is a third option that lets you connect with SSH (X forwarding possible, but otherwise no GUI).
Setting up Remmina (recommended option)
This is by far the easiest and most straightforward solution to access the labs. One of you need to be logged in to a LiU linux lab computer (only one student can access a Kali machine through RDP at a time).
- Start Remmina
- Create new connection
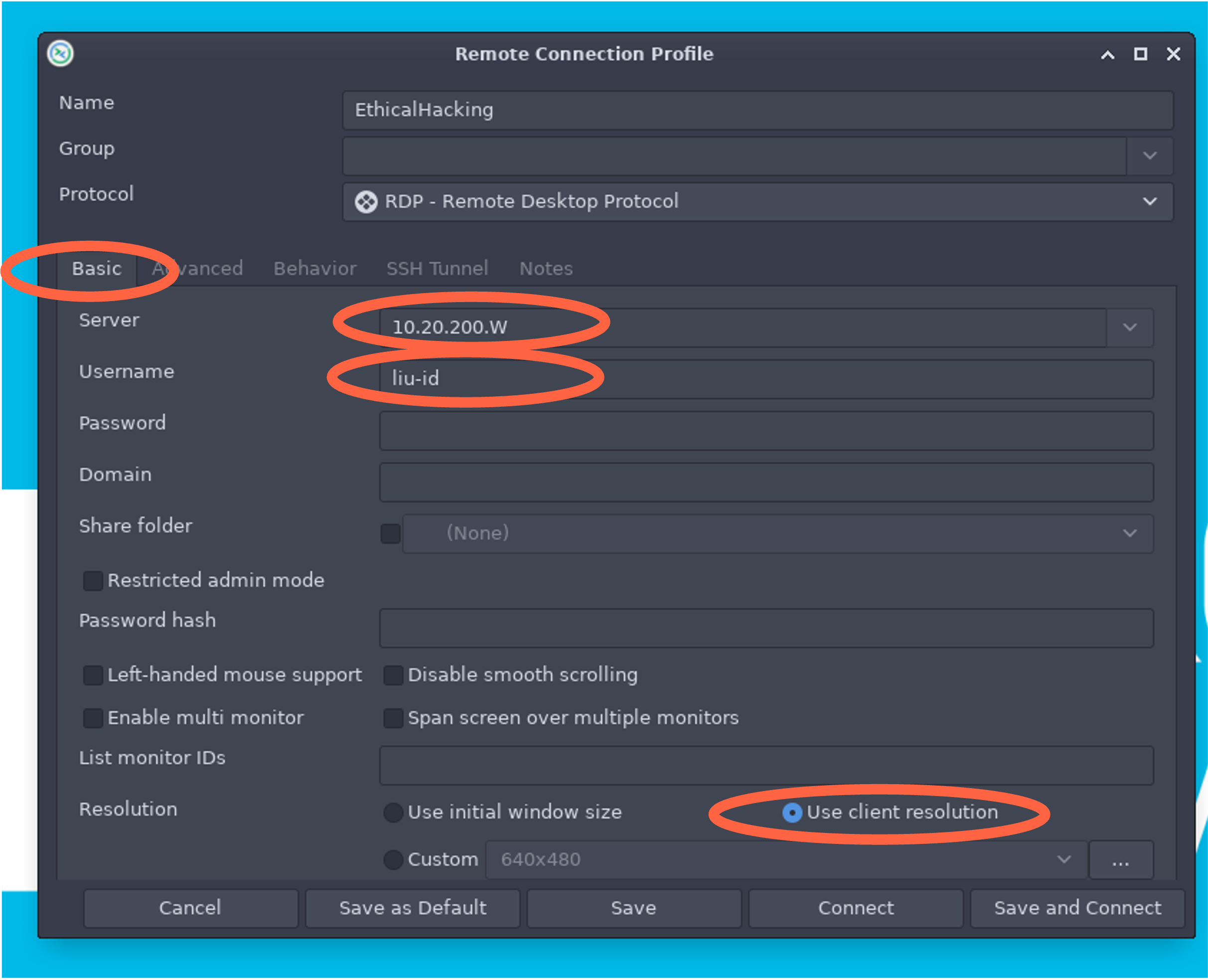
- Under Basic tab (See Fig 1)
- Add Server 10.61.200.W, where W is your world number
- Add username (your liuid)
- Choose Use Client resolution
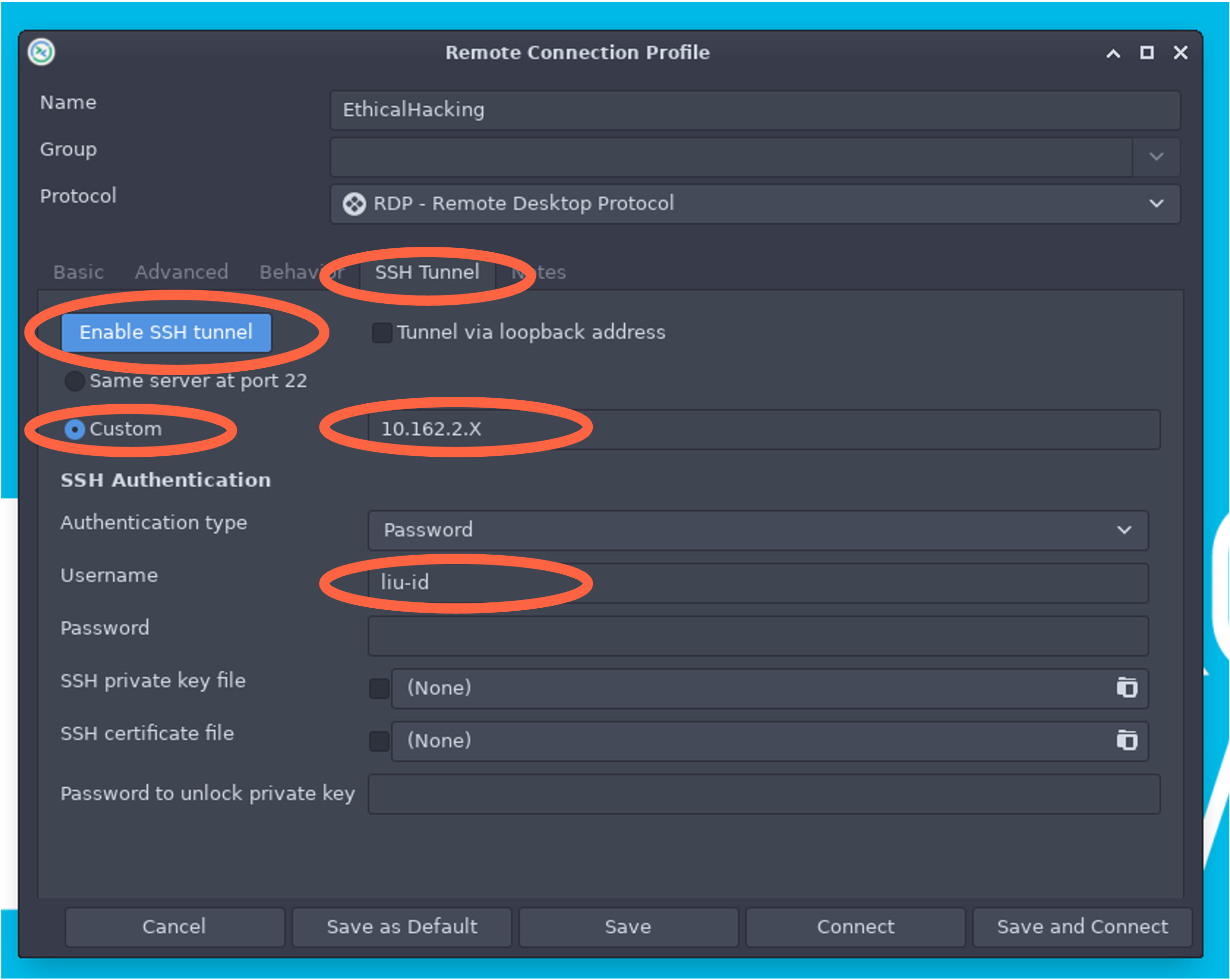
- Under SSH Tunnel (See Fig 2)
- Enable SSH tunnel
- Select Custom
- Enter Server 10.162.2.X, 10.162.2.X is your tunnel IP
- Username (your liuid)
- Save and Connect, you need to provide your login credentials twice
- Once connected to Kali: open up a terminal and start working on the first flag which you find on the tutorial machine:
replacing W with your world numberssh crash-course@10.61.W.7 -p 1337
Working on a VM on your laptop
You are free to use any tools and system you like to perform the labs. However, you will most probably need to use a number of tools that are most easily available on a Linux system. The most convenient option if you want to work on your own machine that we recommend is that you install Kali Linux as a virtual machine on your system. This has two benefits. Kali Linux offers a wide range of penetration testing tools out of the box, and you can install new tools without having to worry about them cluttering up your regular setup.
We will help you with basic setup for this options, but if you run into strange bugs, we will not provide extensive support, but instead will refer you to the recommended option.
To install Kali Linux as a virtual machine you should carry out these steps:
- Download and install Virtualbox (other virtualization environments also exist)
- Grab a copy of the Kali Linux Virtualbox Image
- Open Virtualbox and select "Machine" -> "Add"
- Choose the .vbox file from the unzipped folder and select "Open"
- Start the VM and use the default username and password both being "kali"
If you have a Mac with Apple silicon (M1 or M2 chips), you can run Kali on UTM (an alternative to VirtualBox) by following this guide, or this guide. Additionally, Kali does provide their own instructions on how to set it up. If you have issues with a black screen on start, this video shows a fix.
Once you have your local Kali VM setup, you need to complete the following steps to connect to the lab environment
- Download this script
- Edit the script to fill in your individual details. Note that each student has their own info, you cannot use the same as your lab partner. Moreover, some information is specific to your VM, so you will need to look those up yourself.
- Make sure the script has executable permissions,
chmod +x setup-network.sh - Run the script with root privileges:
sudo ./setup-network.sh - Start the tunnel (as normal user):
where T is your tunnel, liuid is your liu ID, and 10.162.2.X is your tunnel IP. You can ignore the message telling you that the directory does not existssh -w0:T liuid@10.162.2.X -f true - You can now start working on the first flag which you find on the tutorial machine:
replacing W with your world numberssh crash-course@10.61.W.7 -p 1337
If you reboot your VM, then you need to redo steps 3 and 4. If you leave your VM running but the network connection is broken, then the tunnel will close. If you run ps ax | grep ssh you can see if the tunnel is active or not. If the tunnel is no longer active you need to run step 4 again.
Logging in with SSH through a jump host
You can run this command from any machine connected to the LiU network to connect to a machine that is in the 10.61.0.0/16 range:
ssh -J liuid@10.162.2.X user@destination
ssh -J liuid@10.162.2.X liuid@10.261.200.W
ssh -J liuid@10.162.2.X crash-course@10.61.W.7 -p 1337
Flag topics
There are 13 flags with a total of 100 possible points. The topics and learning goals of each flag is provided in the table below. Please note that the flag points have not yet been updated for 2026
| Number | Prefix | Topic | Flag type | Points | Learning outcomes |
|---|---|---|---|---|---|
| 1 | 155d78 | Tutorial flag | Regular | 5 | - Perform reconnaissance and discovery to plan operations - access credentials, such as account names, passwords and access tokens - collect and exfiltrate data from computing environments |
| 2 | b9f737 | Hidden in plain sight | Regular | 3 |
- Perform reconnaissance and discovery to plan operations - Data decoding |
| 3 | c0b4f6 | Caffeine injection | Regular | 4 |
– Perform reconnaissance and discovery to plan operations. – Collect and exfiltrate data from computing environments. |
| 4 | 4a263c | Let’s dance | Regular | 6 |
- Perform reconnaissance and discovery to plan operations. – Collect and exfiltrate data from computing environments. |
| 5 | 90b353 | Call the manager | Regular | 6 |
- Perform reconnaissance and discovery to plan operations - access credentials, such as account names, passwords and access tokens - achieve initial access to networks and systems |
| 6 | cd699a | Remote exploitation | Regular | 6 |
- Perform reconnaissance and discovery to plan operations - achieve initial access to networks and systems - execute malicious code on remote devices - establish command and control capabilities to communicate with compromised systems - persist on networks by maintaining access across interruptions - move laterally, pivoting through the computing environment |
| 7 | 6d99c7 | Command injection | Regular | 6 | |
| 8 | f9038f | Lateral movement | Regular | 9 |
- Perform reconnaissance and discovery to plan operations - access credentials, such as account names, passwords and access tokens - achieve initial access to networks and systems - execute malicious code on remote devices - establish command and control capabilities to communicate with compromised systems - move laterally, pivoting through the computing environment - collect and exfiltrate data from computing environments. |
| 9 | 9f1f16 | Privilege escalation | Regular | 8 |
- Collect and exfiltrate data from computing environments - execute malicious code on remote devices - elevate privileges on systems to gain higher-level permissions - avoid detection by network defenders. |
| 10 | 2e98c5 | Substitute user | Regular | 11 |
- Execute malicious code on remote devices. – Elevate privileges on systems to gain higher-level permissions. – Collect and exfiltrate data from computing environments |
| 11 | 14ce18 | Traffic sniffing | Regular | 8 |
- Perform reconnaissance and discovery to plan operations - collect and exfiltrate data from computing environments |
| 12 | 5d402e | Client-side attacks | Regular | 12 |
- Establish resources to support offensive security operations - achieve initial access to networks and systems - execute malicious code on remote devices - establish command and control capabilities to communicate with compromised systems - persist on networks by maintaining access across interruptions - move laterally, pivoting through the computing environment |
| 13 | 61075a | Icarus | Advanced | 16 |
- Perform reconnaissance and discovery to plan operations - Establish resources to support offensive security operations - Develop exploits |
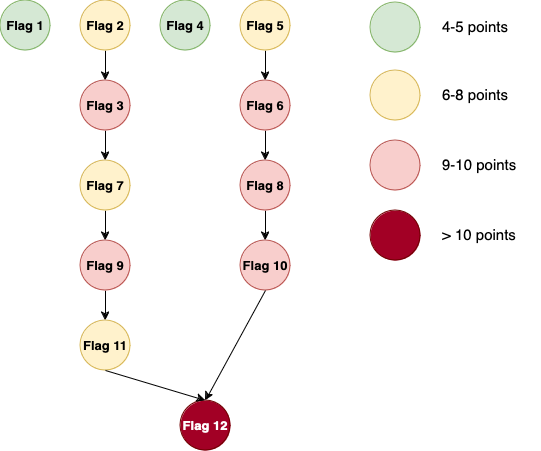
Flag dependencies
Hints points and dates
Note: these dates are still tentative for VT2, and will be finalized before VT2 start. Announcements might also be delayed later during the course (e.g., due to issues with the infrastructure).
| Time of announcement | Flag number | Hint | Point deduction |
|---|---|---|---|
| 2026-02-19 17.00 | 2 | 1 | 1 |
| 2026-02-23 17.00 | 2 | 2 | 1 |
| 2026-02-26 17.00 | 3 | 1 | 1 |
| 2026-02-26 17.00 | 4 | 1 | 2 |
| 2026-03-02 17.00 | 3 | 2 | 1 |
| 2026-03-02 17.00 | 4 | 2 | 2 |
| 2026-03-04 17.00 | 5 | 1 | 2 |
| 2026-03-06 17.00 | 5 | 2 | 2 |
| 2026-03-11 17.00 | 6 | 1 | 1 |
| 2026-03-13 17.00 | 6 | 2 | 2 |
| 2026-03-23 17.00 | 6 | 3 | 1 |
| 2026-04-07 17.00 | 7 | 1 | 1 |
| 2026-04-09 17.00 | 8 | 1 | 2 |
| 2026-04-09 17.00 | 7 | 2 | 1 |
| 2026-04-13 17.00 | 7 | 3 | 2 |
| 2026-04-15 17.00 | 8 | 2 | 2 |
| 2026-04-20 17.00 | 9 | 1 | 2 |
| 2026-04-20 17.00 | 8 | 3 | 3 |
| 2026-04-24 17.00 | 9 | 2 | 1 |
| 2026-04-30 17.00 | 9 | 3 | 3 |
| 2026-04-30 17.00 | 10 | 1 | 2 |
| 2026-05-04 17.00 | 11 | 1 | 2 |
| 2025-05-05 17.00 | 10 | 2 | 3 |
| 2025-05-07 17.00 | 10 | 3 | 4 |
| 2025-05-08 17.00 | 11 | 2 | 4 |
| 2025-05-12 17.00 | 12 | 1 | 1 |
| 2025-05-14 17.00 | 12 | 2 | 1 |
| 2025-05-18 17.00 | 12 | 3 | 2 |
| 2025-05-19 17.00 | 13 | 1 | 2 |
| 2025-05-22 17.00 | 12 | 4 | 6 |
| 2025-05-22 17.00 | 13 | 2 | 3 |
| 2025-05-25 17.00 | 13 | 3 | 4 |
| 2025-05-28 17.00 | 13 | 4 | 5 |
Point policy for misconfigured flags
We encourage creativity and out-of-the box thinking. In many cases there are several ways of finding a flag, which is similar to real life and just how we like it. However, if you find a flag with a method which is subsantially easier than the original design, the following policy will be applied. Submitting the flag and informing us about the issue will reward you a number of points which is less than the full points for the flag (exact amount will be decided based on the particular case). We will then try to patch the issue, allowing you to again find the flag in the intended manner. When you then again report the flag, you will receive full points for the flag so that the total points you receive is higher than the original number of points for the flag.
Page responsible: Mikael Asplund
Last updated: 2026-02-04

