
Mohammad Borhani
PhD student
About me
I received an M.Sc. degree in Software Engineering from Mälardalen University, Sweden, where I completed an industrial master's thesis with ABB in Västerås. I was an Erasmus+ International Credit Mobility (ICM) student at Mälardalen University. I also hold an M.Sc. degree in Computer Engineering from the School of Electrical and Computer Engineering, University of Tehran, where I graduated with an A-level MSc score. Additionally, I was the top graduate in my B.Sc. program. Currently, I am a third-year Ph.D. student at Linköping University in the Department of Computer and Information Science. My main research interests include VPN, SDN, network security, and communication network optimization.
Research
- Communication Networks
- Network Optimization
- VPLS
- SDN
- HIP
Education
- MSc in Computer Science, 2021
- Mälardalens University, (Industrial Thesis with ABB Sweden)
- Msc In Computer Engineering, 2020
- University of Tehran, Iran
Recent Publications
A critical analysis of the industrial device scanners’ potentials, risks, and preventives -- Journal of Industrial Information Integration-2024
Industrial device scanners allow anyone to scan devices on private networks and the Internet. They were intended as network security tools, but they are commonly exploited as attack tools, as scanning can reveal vulnerable devices. However, from a defensive perspective, this vulnerability disclosure could be used to secure devices if characteristics such as type, model, manufacturer, and firmware could be identified. Automated scanning reports can help to apply security measures before an attacker finds a vulnerability. A complete device recognition procedure can then be seen as the basis for auditing networks and identifying vulnerabilities to mitigate cyber-attacks, especially among Industrial Internet of Things (IIoT) devices that are part of critical systems. In this survey, considering SCADA (Supervisory Control and Data Acquisition) systems as monitoring and control components of essential infrastructure, we focus on analyzing the architectures, specifications, and constraints of several industrial device scanners. In addition, we examine the information revealed by the scanners to identify the threats posed by them on industrial systems and networks. We analyze monthly and yearly statistics of cyber-attack incidents to investigate the role of these scanners in accelerating attacks. By presenting the findings of an experimentation, we highlight how easily anyone could identify hundreds of Internet-connected industrial devices in Sweden, which could lead to a major service interruption in industrial environments designed for minimal human involvement. We also discuss several methods to avoid scanners or reduce their identifying capabilities to conceal industrial devices from unauthorized access.
PDF
KDC Placement Problem in Secure VPLS Networks -- IEEE Transactions on Information Forensics and Security-2023
Virtual Private LAN Service (VPLS) is a VPN technology that connects remote client sites with provider networks in a transparent manner. Session key-based HIPLS (S-HIPLS) is a VPLS architecture based on the Host Identity Protocol (HIP) that provides a secure VPLS architecture using a Key Distribution Center (KDC) to implement security mechanisms such as authentication, encryption, etc. It exhibits limited scalability though. Using multiple distributed KDCs would offer numerous advantages including reduced workload per KDC, distributed key storage, and improved scalability, while simultaneously eliminating the single point of failure of S-HIPLS. It would also come with the need for optimally placing KDCs in the provider network. In this work, we formulate the KDC placement (KDCP) problem for a secure VPLS network as an Integer Linear Programming (ILP) problem. The latter is NP-hard, thereby suggesting a high computational cost for obtaining exact solutions especially for large deployments. Therefore, we motivate the use of a primal-dual algorithm to efficiently produce near-optimal solutions. Extensive evaluations on large-scale network topologies, such as the random Internet graph, demonstrate our method’s time-efficiency as well as its improved scalability and usefulness compared to both HIPLS and S-HIPLS.
PDF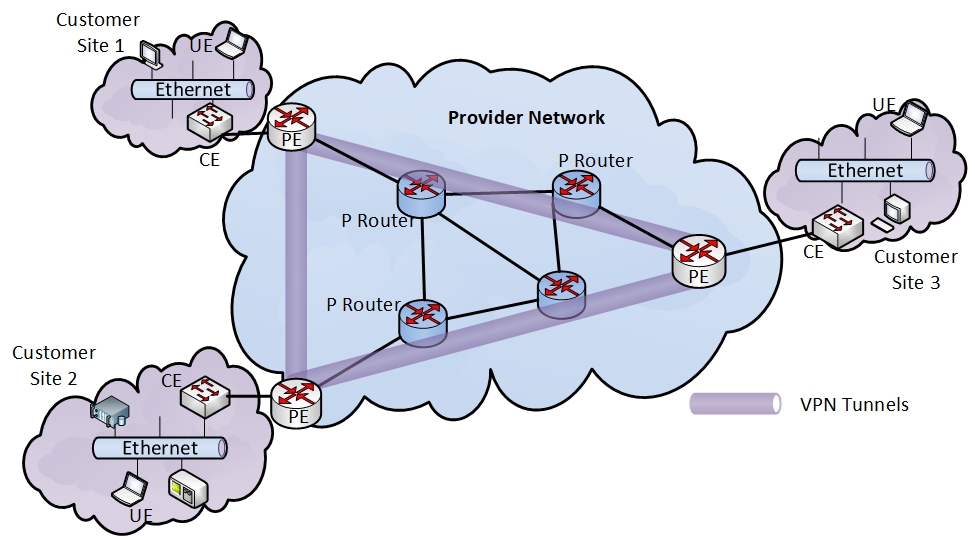
Optimization of Relay Placement for Scalable Virtual Private LAN Services -- FIRA-SIGCOMM-2022
Virtual Private LAN Services are becoming popular for securely connecting geographically dispersed devices to a common protected LAN network isolated from the rest of the Internet. Traditional IP routing protocols cannot provide such connectivity; thus an overlay network of encrypted HIP/IPsec tunnels can be used instead. However, the number of full-mesh tunnels between communicating devices grows exponentially to the number of devices thereby suggesting the investigation of alternatives. The introduction of relaying, which entails selecting a subset of hub routers to retain full-mesh connectivity, allows non-hub routers, the so-called spokes, to maintain connectivity via a hub. In this work, we study the effect of relay-based routing that minimizes the number of hubs, the connection cost between spokes and hubs, the cost of connecting hubs, and the hubs deployment cost. Additionally, we prove that this minimization problem is NP-hard and, thus, intractable for large scale networks. Therefore, we propose an algorithm with provable guarantees that provides an approximate but efficient solution. Initial simulation results indicate a reduction by more than 90% in the memory required for routing tables at the expense of a minor increase in the tunnel path length.
PDF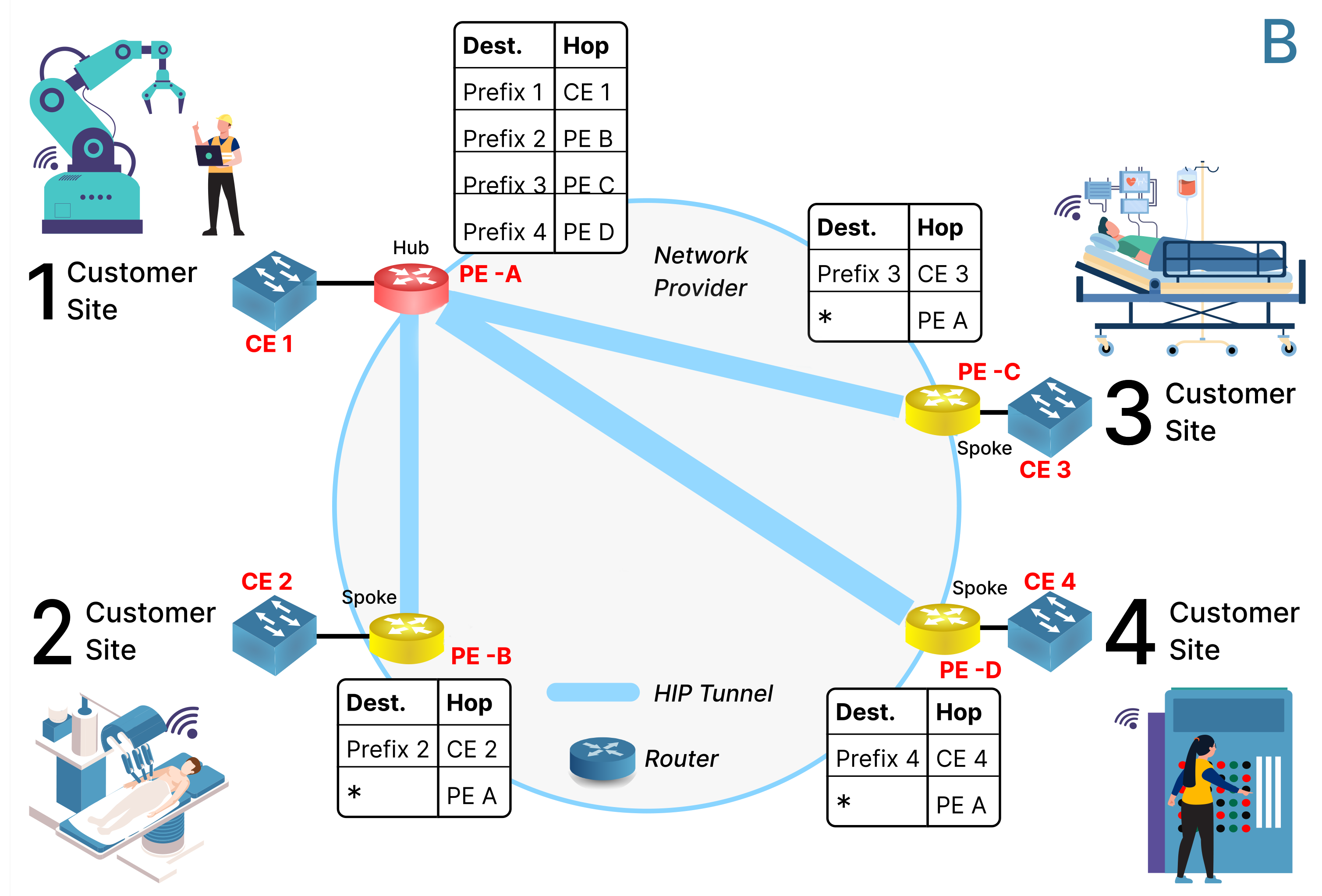
A Survey of Virtual Private LAN Services (VPLS): Past, Present and Future -- Computer Networks-2021
Virtual Private LAN services (VPLS) is a Layer 2 Virtual Private Network (L2VPN) service that has gained immense popularity due to a number of its features, such as protocol independence, multipoint-to-multipoint mesh connectivity, robust security, low operational cost (in terms of optimal resource utilization), and high scalability. In addition to the traditional VPLS architectures, novel VPLS solutions have been designed leveraging new emerging paradigms, such as Software Defined Networking (SDN) and Network Function Virtualization (NFV), to keep up with the increasing demand. These emerging solutions help in enhancing scalability, strengthening security, and optimizing resource utilization. This paper aims to conduct an in-depth survey of various VPLS architectures and highlight different characteristics through insightful comparisons. Moreover, the article discusses numerous technical aspects such as security, scalability, compatibility, tunnel management, operational issues, and complexity, along with the lessons learned. Finally, the paper outlines future research directions related to VPLS. To the best of our knowledge, this paper is the first to furnish a detailed survey of VPLS.
PDF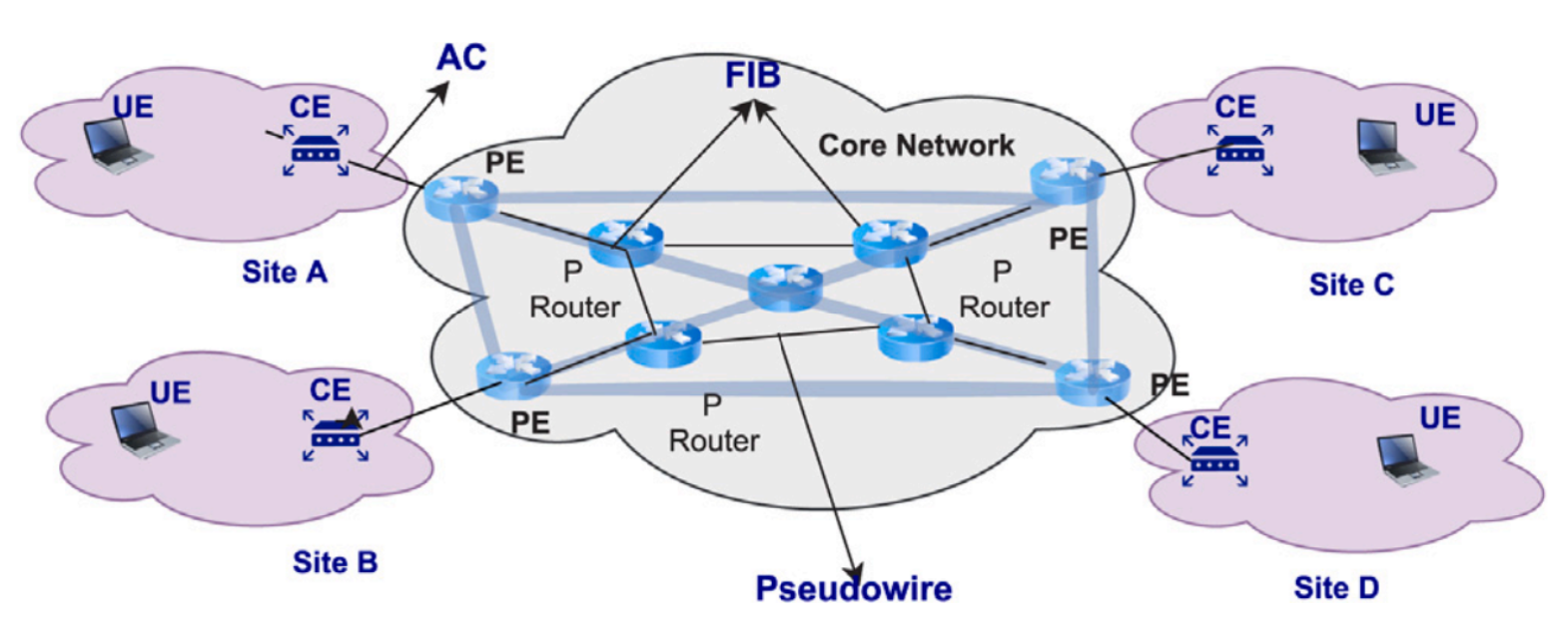
Secure and Resilient Communications in the Industrial Internet -- Book Chapter: Guide to Disaster-Resilient Communication Networks-2020
The Industrial Internet brings the promise of increased efficiency through on-demand manufacturing and maintenance, combining sensors data from engines and industrial devices with big data analysis in the cloud. In this chapter, we survey the main challenges that the Industrial Internet faces from a networking viewpoint. We especially focus on security, as critical industrial components could be exposed over the Internet, affecting resilience. We describe two approaches, Identity-Defined Networking and Software-Defined Virtual Private LAN Services as potential network architectures for the Industrial Internet.
PDF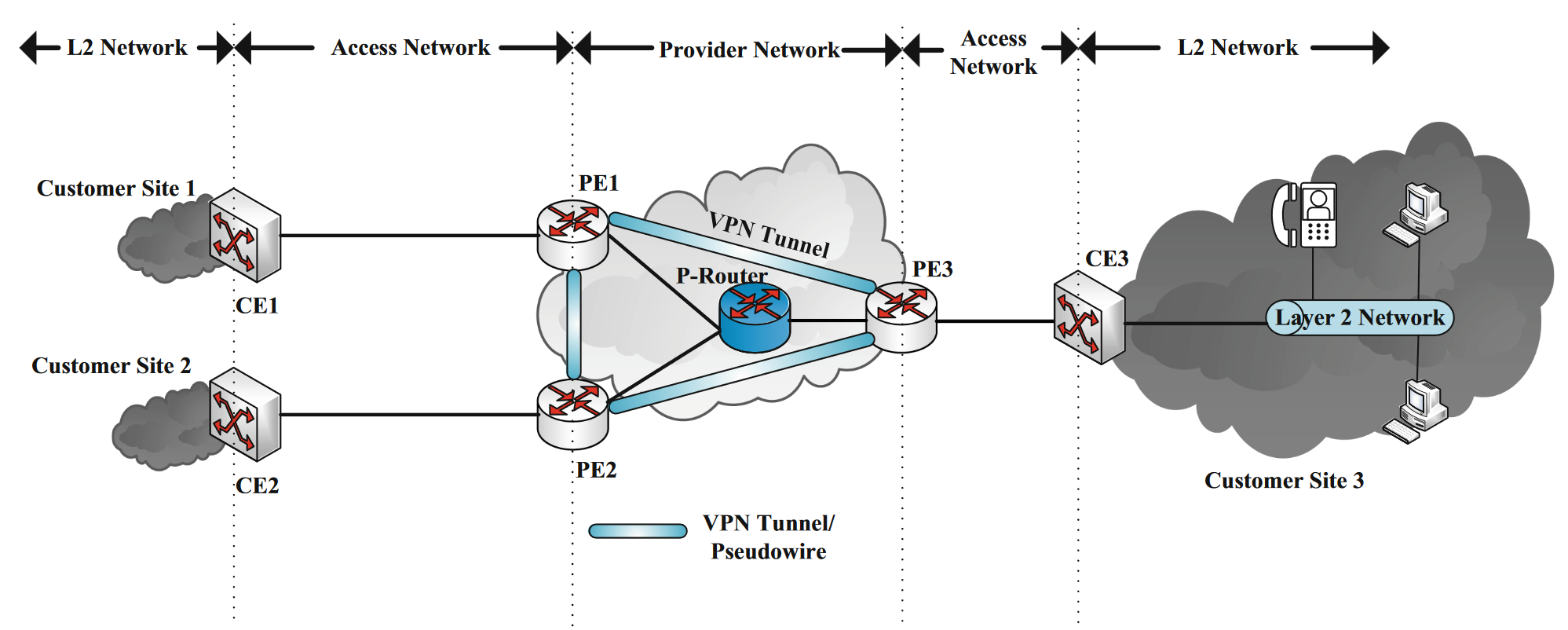
Multi-Armed Bandit Learning for Cache Content Placement in Vehicular Social Networks -- IEEE Communications Letters-2019
In this letter, the efficient dissemination of content in a socially-aware cache-enabled hybrid network using multi-armed bandit learning theory is analyzed. Specifically, an overlay cellular network over a vehicular social network is considered, where commuters request for multimedia content from either the stationary road-side units (RSUs), the base station, or the single mobile cache unit (MCU), if accessible. Firstly, we propose an algorithm to optimally distribute popular contents among the locally deployed RSU caches. To further maximize the cache hits experienced by vehicles, we then present an algorithm to find the best traversal path for the MCU based on commuters' social degree distribution. For performance evaluation, the asymptotic regret upper bounds of the two algorithms are also derived. Simulations reveal that the proposed algorithms outperform existing content placement methods in terms of overall network throughput.
PDF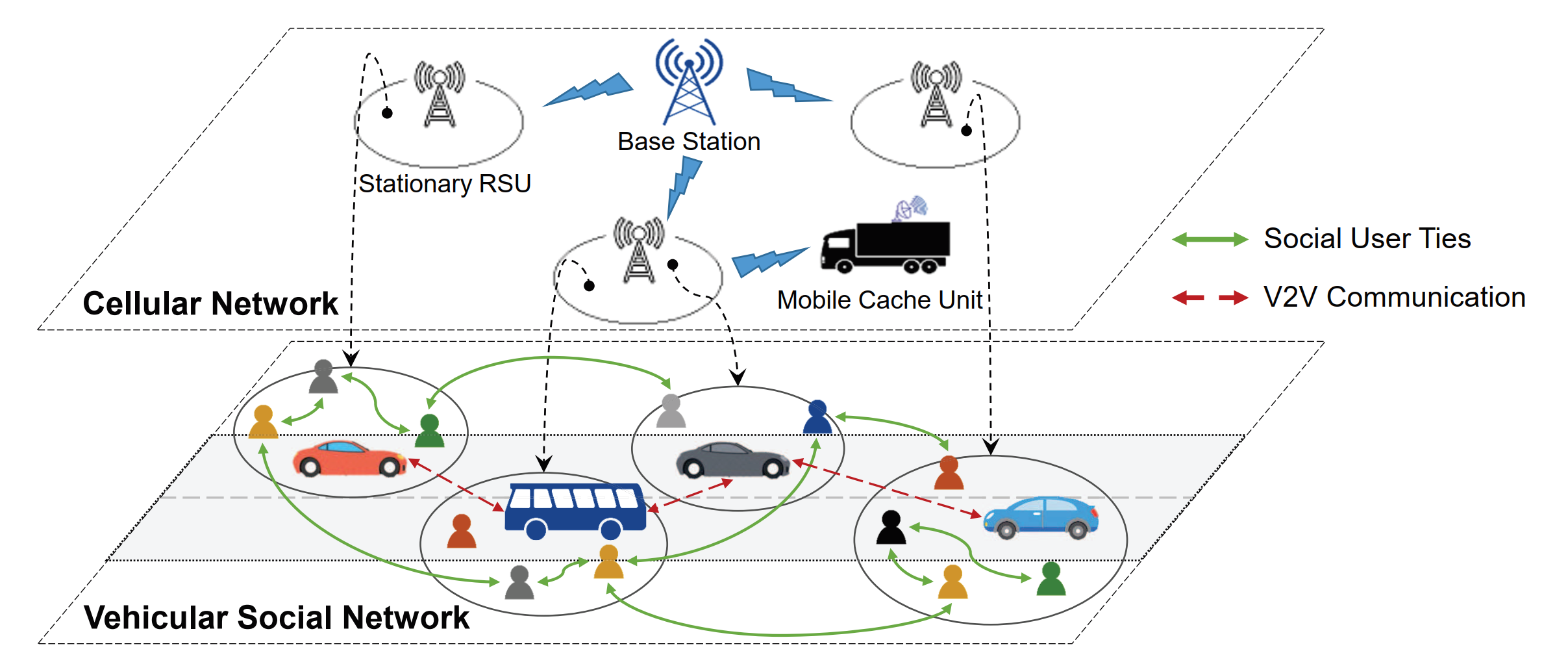
News
- June 2022: Paper acceptance -- FIRA-SIGCOMM2022
- Feb 2023: Paper acceptance -- IEEE Transactions on Information Forensics and Security
- Apr 2024: Paper acceptance -- Journal of Industrial Information Integration